- Forms Authentication. Using this provider causes unauthenticated requests to be redirected to a specified HTML form using client side redirection. The user can then supply logon credentials, and post the form back to the server. If the application authenticates the request (using application-specific logic), ASP.NET issues a cookie that contains the credentials or a key for reacquiring the client identity. Subsequent requests are issued with the cookie in the request headers, which means that subsequent authentications are unnecessary.
- Passport Authentication. This is a centralized authentication service provided by Microsoft that offers a single logon facility and membership services for participating sites. ASP.NET, in conjunction with the Microsoft® Passport software development kit (SDK), provides similar functionality as Forms Authentication to Passport users.
- Windows Authentication. This provider utilizes the authentication capabilities of IIS. After IIS completes its authentication, ASP.NET uses the authenticated identity's token to authorize access.
To enable a specified authentication provider for an ASP.NET application, you must create an entry in the application's configuration file as follows:
// web.config file
< authentication mode="[Windows/Forms/Passport/None]" >
< /authentication >
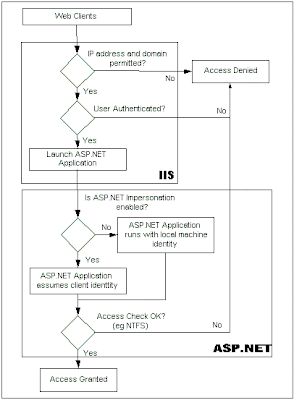
In addition to authentication, ASP.NET provides an impersonation
mechanism to establish the application thread's security token.
Obtaining the correct token relies upon you configuring IIS
authentication, ASP.NET authentication providers, and ASP.NET
impersonation settings appropriately. Figure 2 shows the most likely
combinations between IIS authentication and ASP.NET providers.